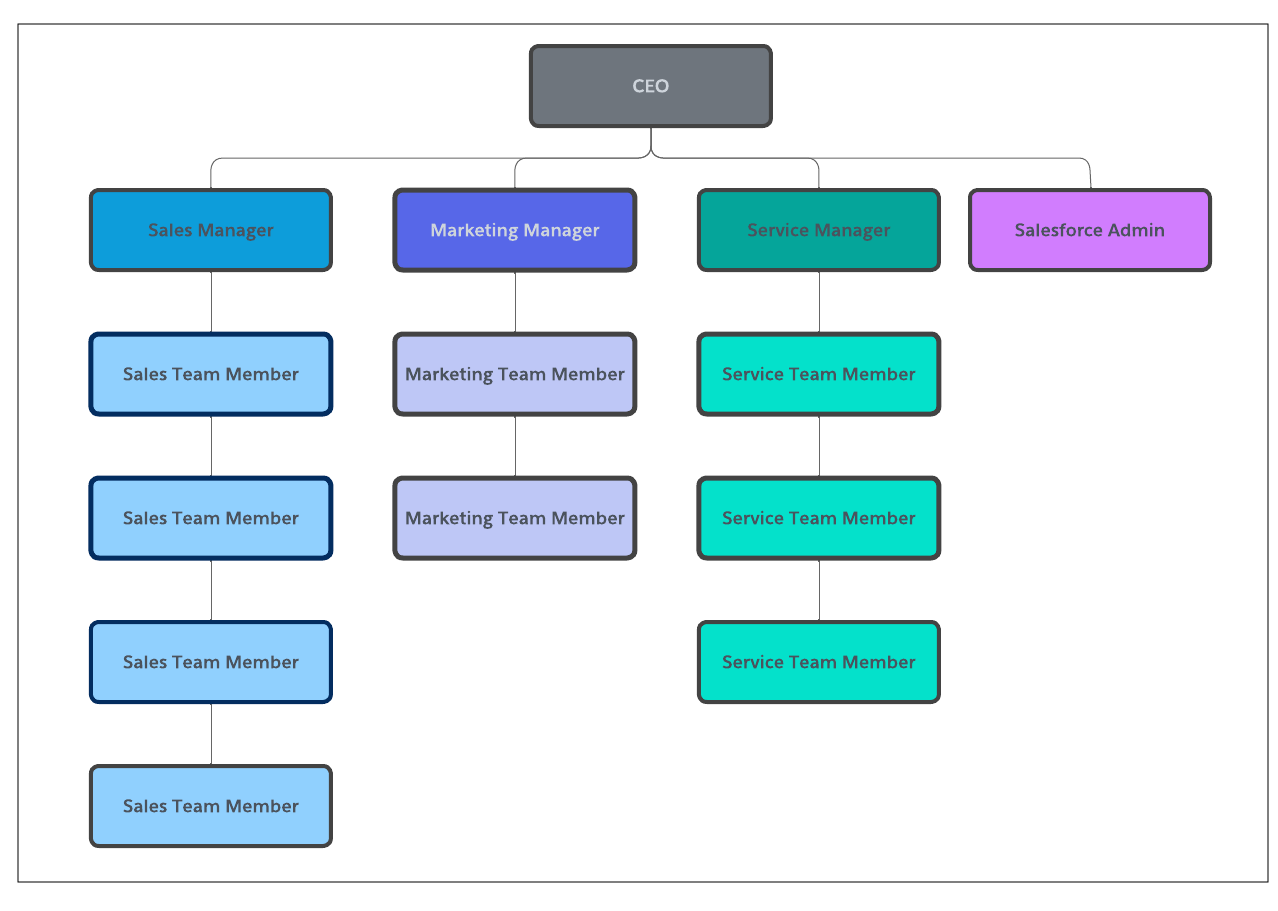
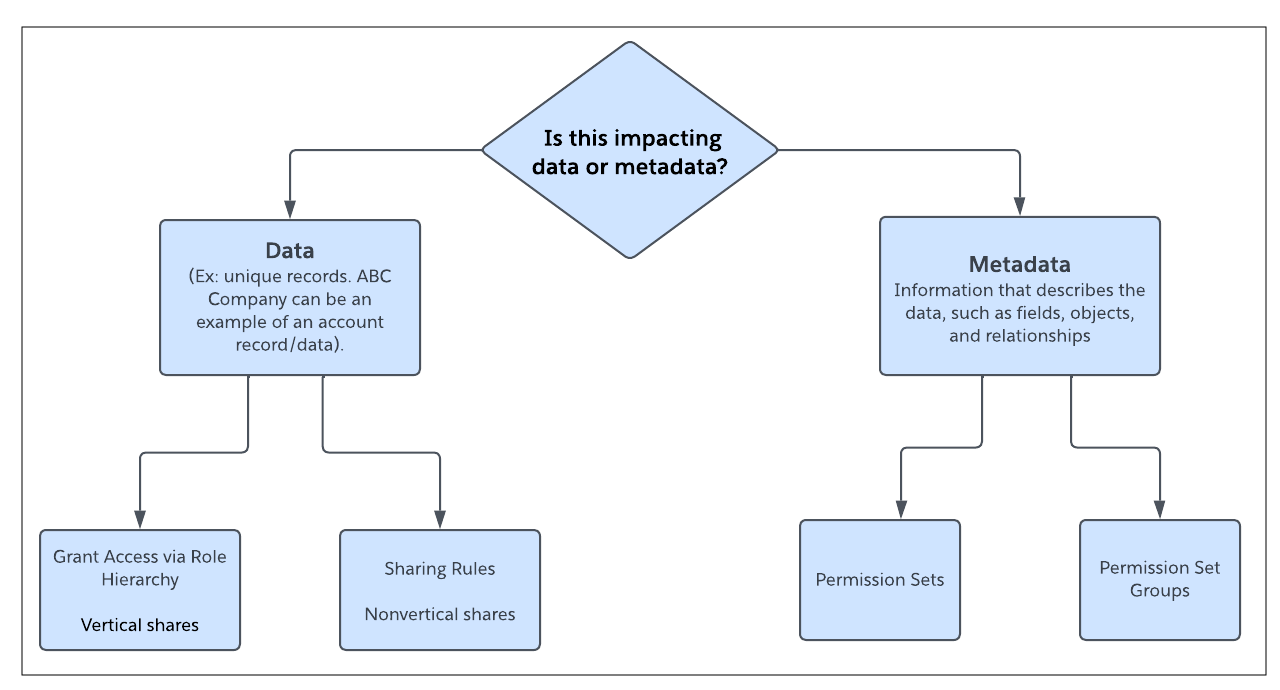
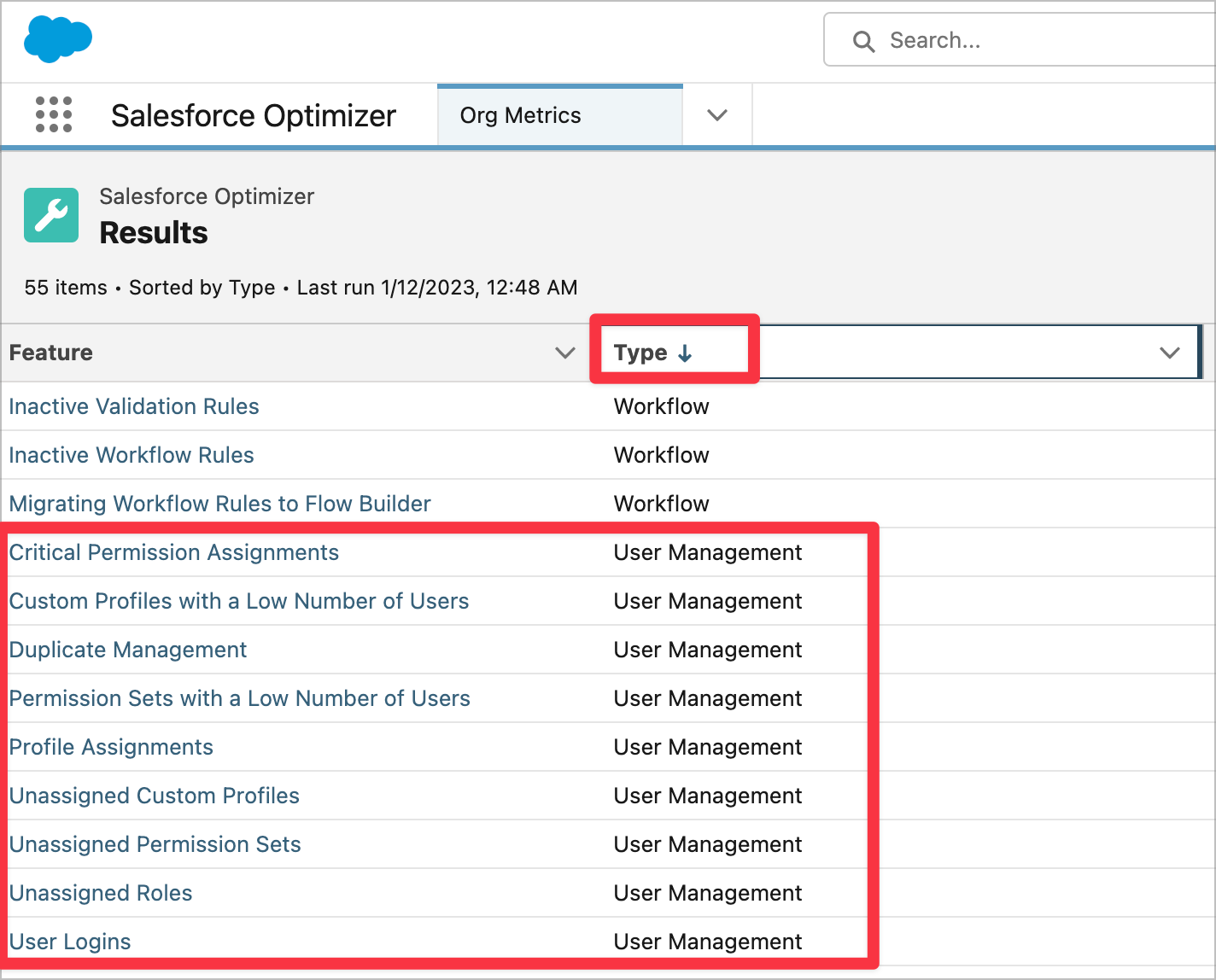
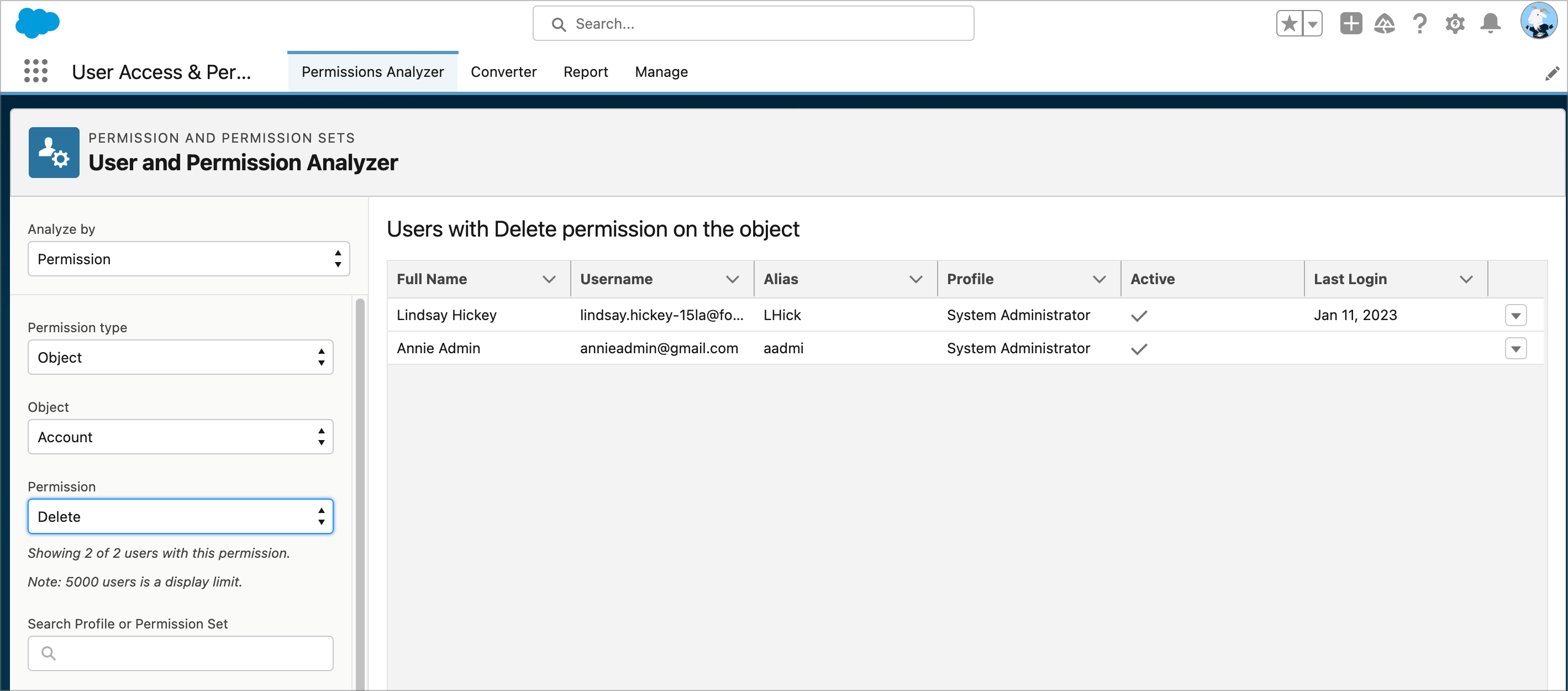
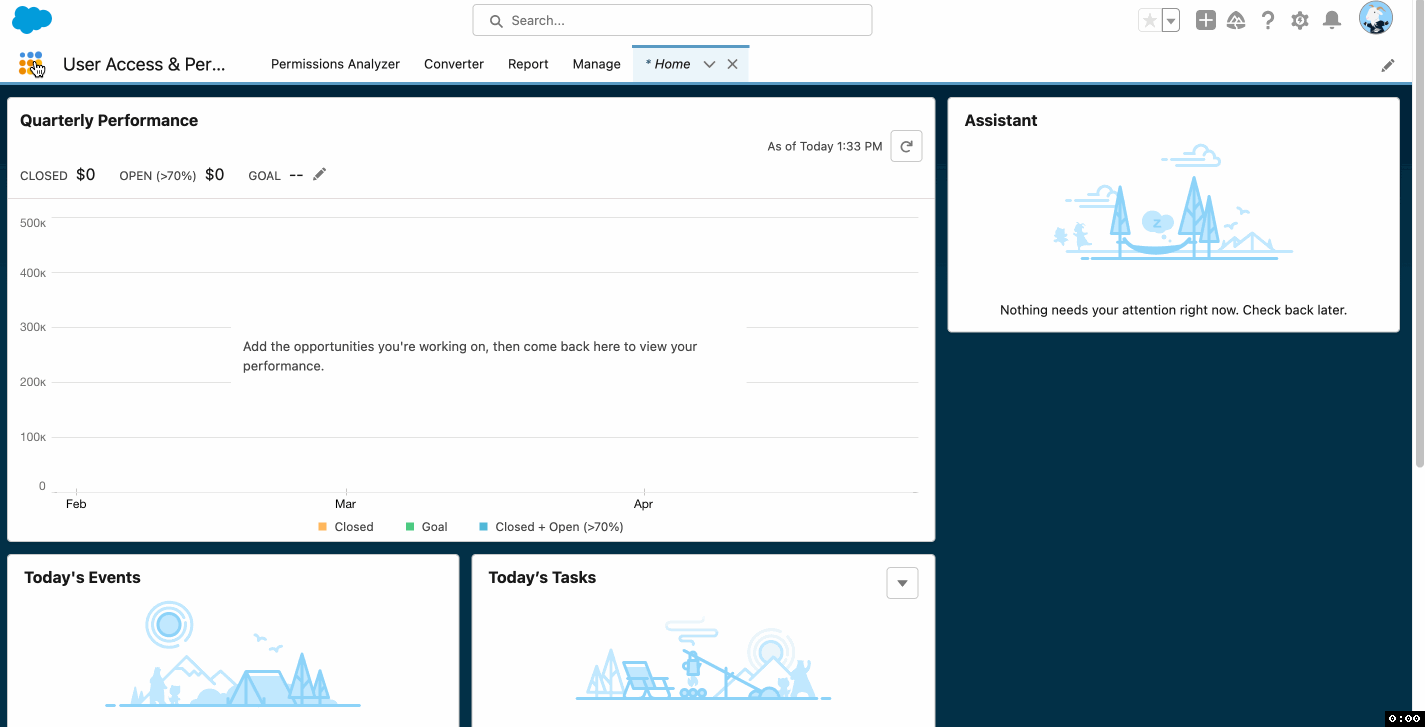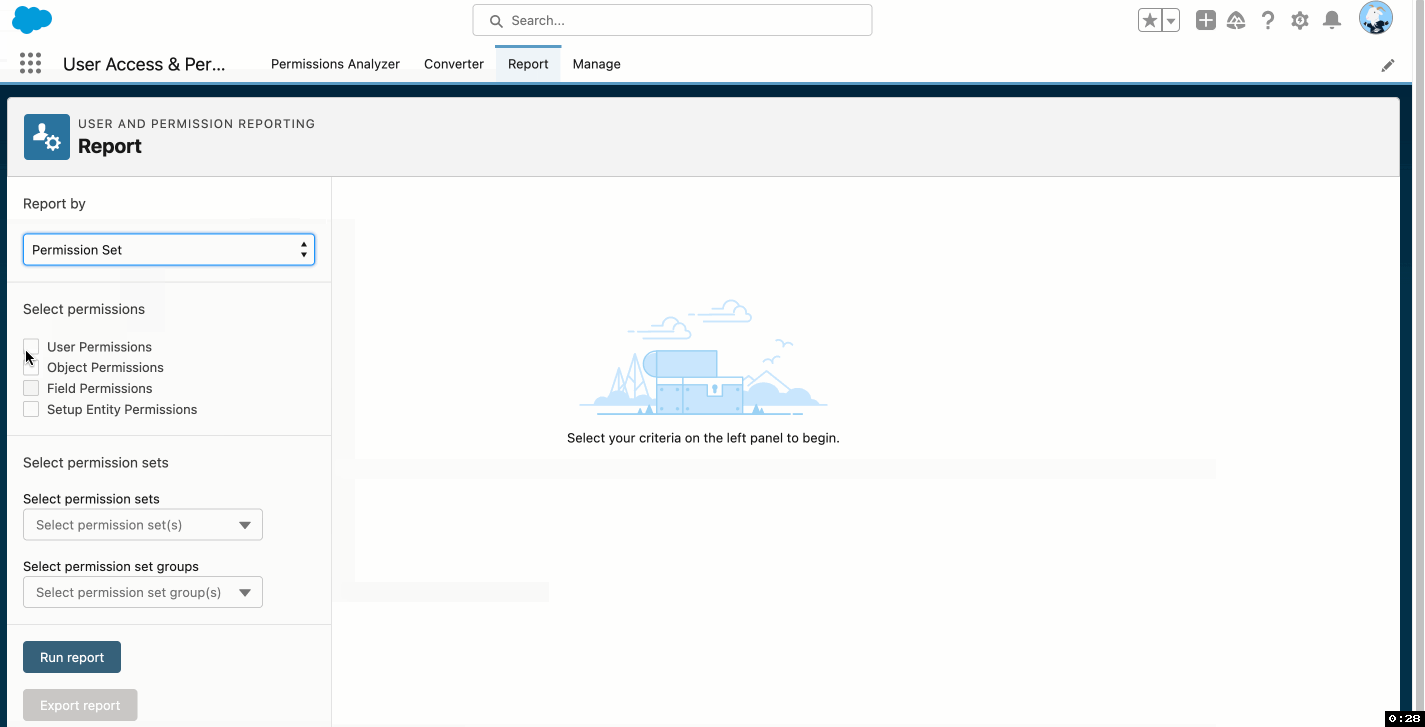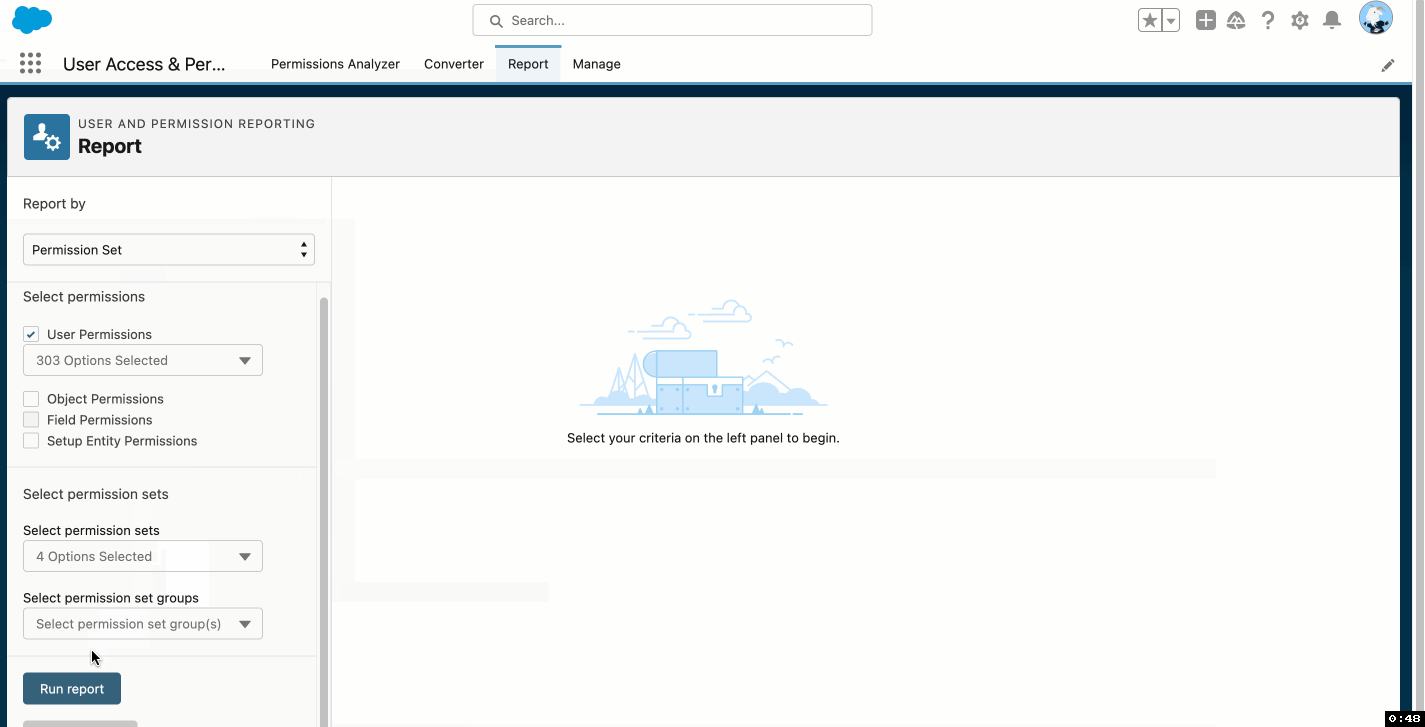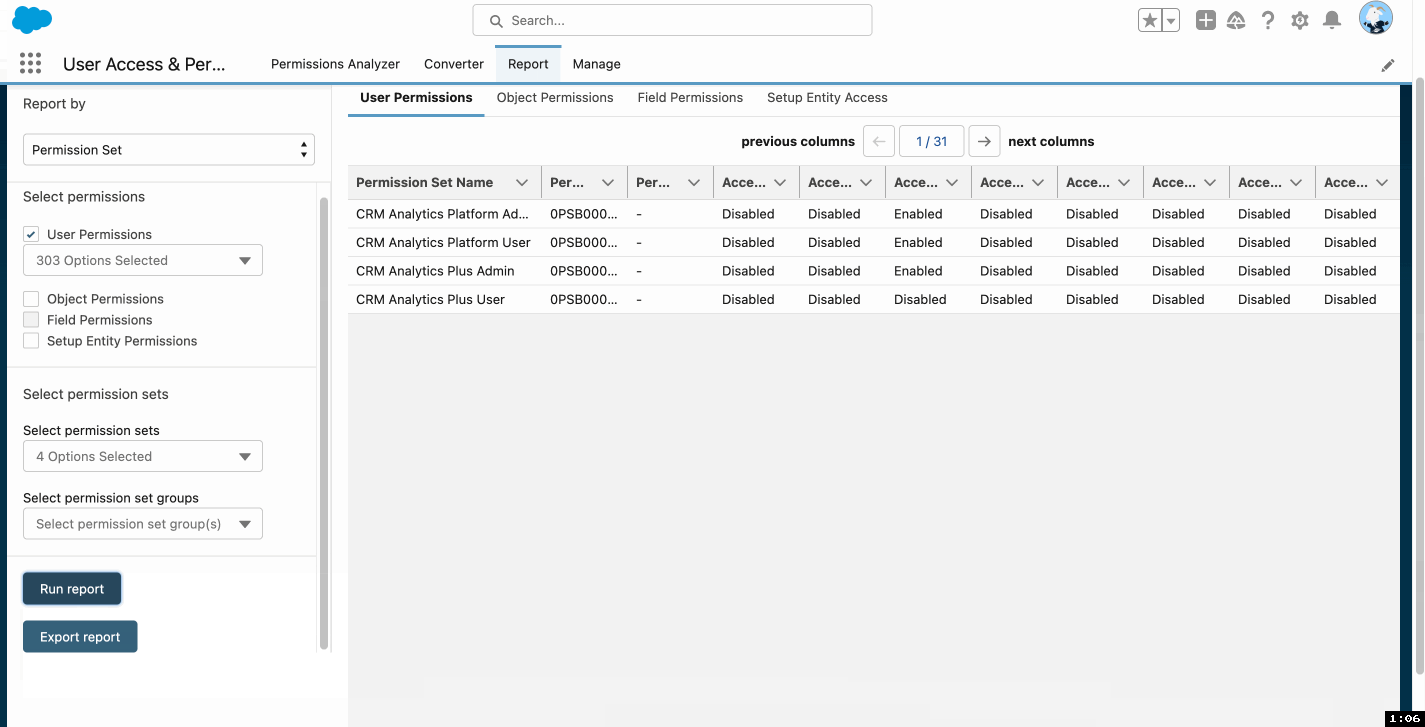
Winter ’25 is almost here! Learn more about user management and check out Be Release Ready to discover more resources to help you prepare for Winter ’25. We’re continuing to innovate in Setup starting with user access and user management. We have several exciting enhancements in store for Winter ’25–many thanks to your feedback and […]