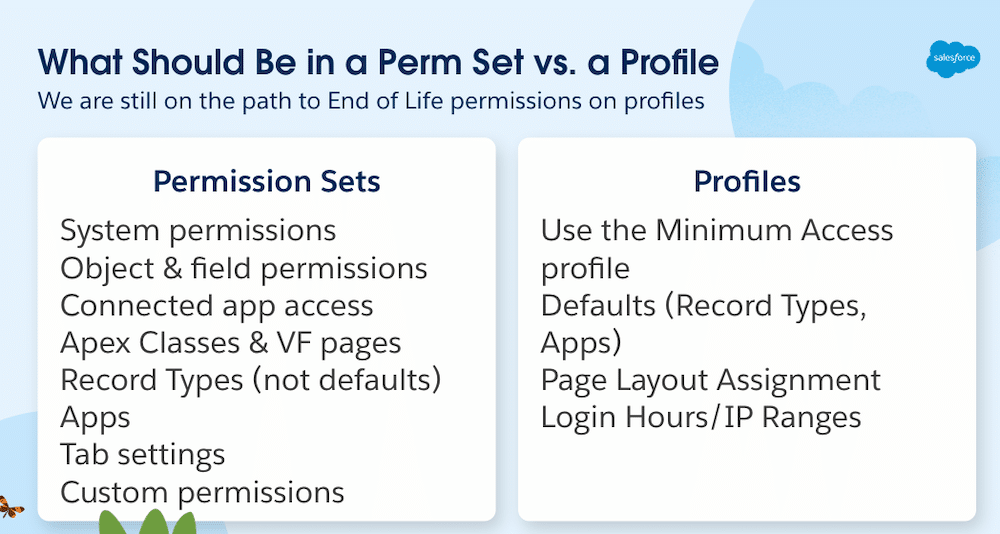
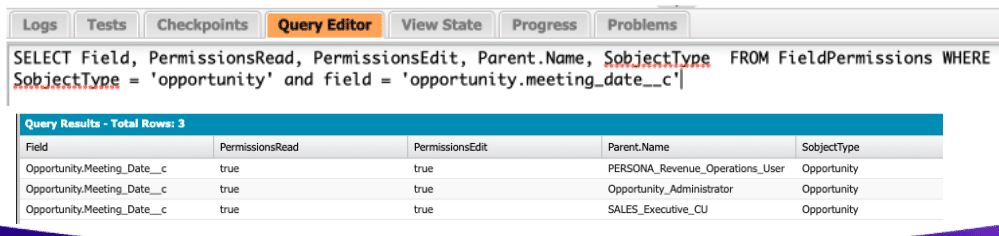
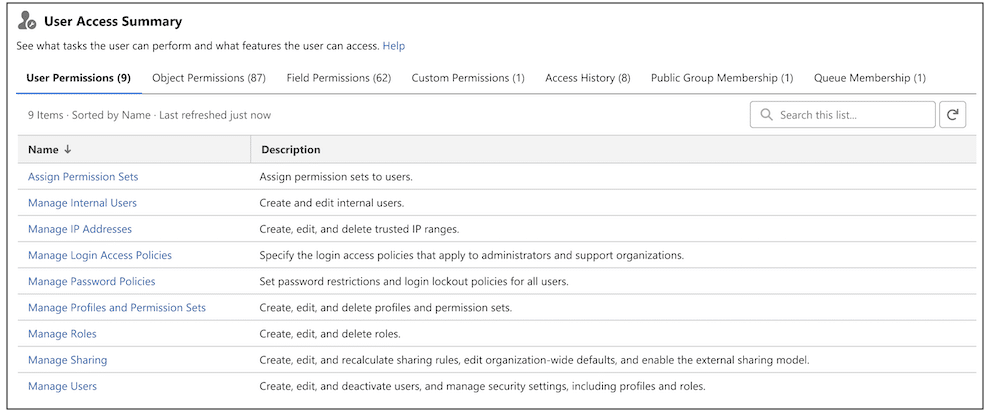
True to the Core Deep Dive has arrived! In this post, we recap the key takeaways from our first episode on Setup and user access. This special monthly series builds on the trusted True to the Core format you know and love, offering you a closer, more focused look at specific Salesforce Platform topics with […]