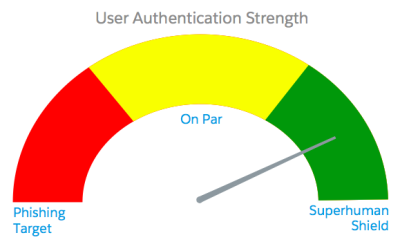
I was recently talking with some new Salesforce Admins who are studying for their certification exam. We discussed how BIG the platform feels and how, with so much to learn, it can feel challenging to even get started. Salesforce is incredibly powerful, which means there are a lot of features and settings, but new admins […]